When you visit a webpage, you might think of its address, like www.cnn.com. That address isn’t really an Internet address though. It’s a domain name — a friendly and memorable shortcut for an Internet Protocol (IP) address. That kind of address is made up of four groups of numbers, called octets. CNN’s actual address (today) is 151.101.1.67. That’s what your browser really goes to.
The mechanism the browser uses to look up the number from the shortcut is called DNS, or Domain Name System. One of the most resilient and important parts of the Internet, DNS is often provided by your Internet service, whose own servers sync with other DNS servers around the world, providing a distributed system of record — a phone book, if you’d like, for instant address look-ups.
Importantly, DNS is first provided by your computer (or mobile device) that forwards DNS requests from the browser, to your router or modem, which forwards the request to your Internet provider, etc… If you don’t like your Internet provider’s answers (or the speed with which they answer), you can choose a different DNS provider by making a configuration change downstream (eg: on your router, or on your computer.)
This “chain of trust” allows organizations to filter the Internet within the network they provide internally. If an organization doesn’t want its members to visit a website (like pornography) they can insert DNS records locally that prevent the request from actually finding that website.
This is also the basis of many parental controls systems. They keep a list of addresses kids probably shouldn’t go to, and all you have to do is configure your local environment to use the parental controls DNS server, rather than a public unfiltered one. This chain, and the ability for administrators to control the chain, is a part of how the Internet was designed: the browser asks the computer, the computer asks the router, the router asks the network provider, the network provider asks the rest of the Internet.
Last year, Mozilla (makers of the FireFox browser) decided to experiment with breaking that chain of trust. Instead of the browser asking the PC (and so on), they decided maybe the browser could go around the chain, and just ask someone that Mozilla decided to trust. They claim this makes people safer, since they can encrypt that request, using a non-standard approach called DNS over HTTPS (DoH). The effect is that intentionally crafted trust chains will be broken. Fine as an experiment, but this month they decided this behavior would be the default for all FireFox users. If you don’t know how to work around it, your parental controls are effectively disabled.
And working around it is possible — but not easy. Because this is not a standard, or even an accepted RFC (the process by which the Internet is evolved through review and consensus), Mozilla gets to impose arbitrary hoops you have to jump through to disable it. The easier they are for you to implement, the easier they are for someone to defeat.
And Mozilla isn’t the only browser maker messing with trust on the Internet. I’ve written before about Google’s attempts to re-make the ‘Net in their own image.
So, how can you filter the Internet at home while bigger groups than you and me are hard at work funneling all traffic through bastardized versions of the Internet where they can monetize your queries? As of late 2019, here’s what still works — and my best guess about how long it will continue to work…
Circle with Disney – another 1-2 years
Circle is a device that you put on your WiFi network that filters actual traffic. Below DNS is the actual routing of data from a website to a device. This path is managed via ARP (Address Resolution Protocol) tables, which tell your router how to get traffic to a given device. Circle needs to know which devices on your network belong to a child (which is a bit of a pain to setup), then it can stop traffic that’s not appropriate.
Unfortunately, Circle is abandoning the one-time purchase device, in favor of a device+service model that will cost you more. If you can still find them, the original Circle is less than $100, and really works well. It also lets you set time limits and curfews from a reasonably friendly app on your phone.
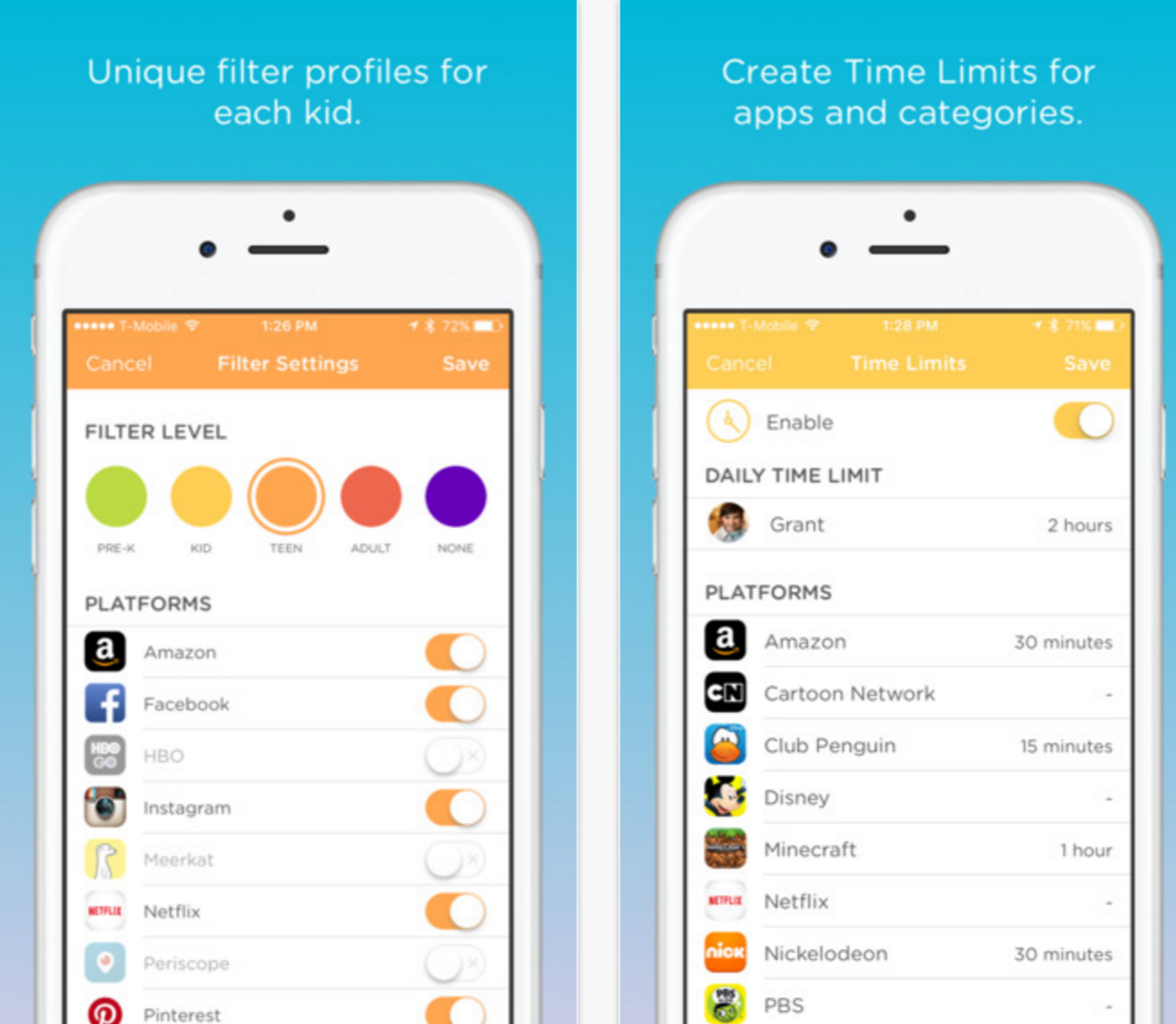
PiHole + OpenDNS – 3-5 years
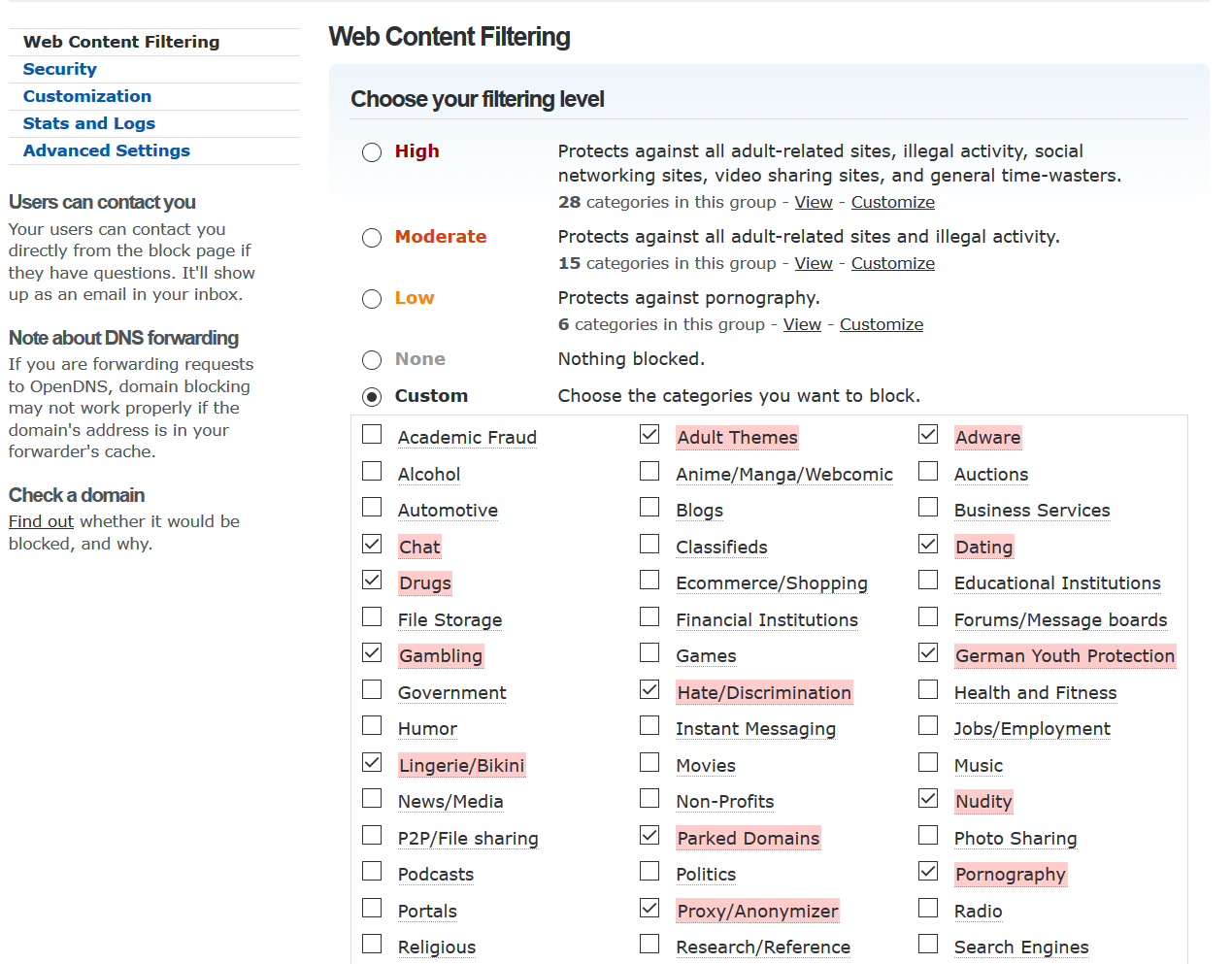
PiHole is a tiny service that runs on a Raspberry Pi. In total it’ll cost you about $50 to set this up on your network. Once the Pi is built and running, you can install PiHole in a couple seconds, and tell it to use OpenDNS as your upstream DNS provider (instead of your Internet provider.) Then tell your router to use the Pi as a DNS server — your own chain of trust. You can then use the OpenDNS website to determine what kinds of web pages should be allowed within your home network.
It sounds complicated, but its really not too hard, and because its actively being developed, they’ve been able to stay on top of changes, like Mozilla just made. As of today, they’ve implemented one of the work-arounds for DoH, that tells the browser not to trust any other DNS provider. Eventually Google is going to realise there’s an untapped data source here, and move to eliminate competition from parents who want to protect their kids. But for the near future, this works well.
Mobile Device Parental Controls – constantly changing
The best phones for parental controls are iPhones… personal preference aside. The Screen Time feature lets you set a PIN and access control for many things on the device. Unfortunately, you need regular physical access to configure and change these settings, which appear and disappear through different OS versions. This obviously requires parents to keep a certain amount of hands-on with their kids devices.
Apple has an app called Apple Configurator that allows you to setup a number of Supervision controls over the device remotely — but they’ve intentionally limited that capability so only organizations (schools or businesses) can use it. They actually research you to determine if you should be allowed to Supervise users before you can use the feature with kid’s devices — presumably they’re monetizing this somehow, because there’s no reason this shouldn’t be free to everyone.
Amazon has a number of features for parental control and monitoring on their tablet devices (yours truly was responsible for some of them), but with each version of their OS, they make those harder to find and use.
Our kids don’t have their own phones…yet. We have one “kid phone” that they can check out if they’re going to an event where we’re not with them — but its locked down tight. Still, their friends all have phones, and the pressure is on. Soon enough, I guess I’ll be trying out some parental control apps, to see what works best outside the home. Any suggestions?

 These are a few of my favorite things from 2018. Abandoned tech is a treasure trove of ideas, both good and bad, and always makes you wonder how the world would be different if a given technology battle had gone another away. Take, for example, this little phone: the Palm Pre3 (by HP.) Although HP had big plans for the platform when they bought the ailing Palm company, a change in leadership resulted in a sudden death for the technology dubbed webOS.
These are a few of my favorite things from 2018. Abandoned tech is a treasure trove of ideas, both good and bad, and always makes you wonder how the world would be different if a given technology battle had gone another away. Take, for example, this little phone: the Palm Pre3 (by HP.) Although HP had big plans for the platform when they bought the ailing Palm company, a change in leadership resulted in a sudden death for the technology dubbed webOS.